JavaScript Security Analysis and Exploitation

This lab involved analyzing a website’s JavaScript code to uncover hidden information, reverse obfuscation, and extract a secret key. The key was then decoded and sent as a POST request to obtain the final flag. (This lab is found on hack the box JavaScript Deobfuscation module )
Step 1: Identifying the JavaScript File
I started by inspecting the HTML source code of the webpage that was given to me. The script tag in the HTML revealed the JavaScript file:
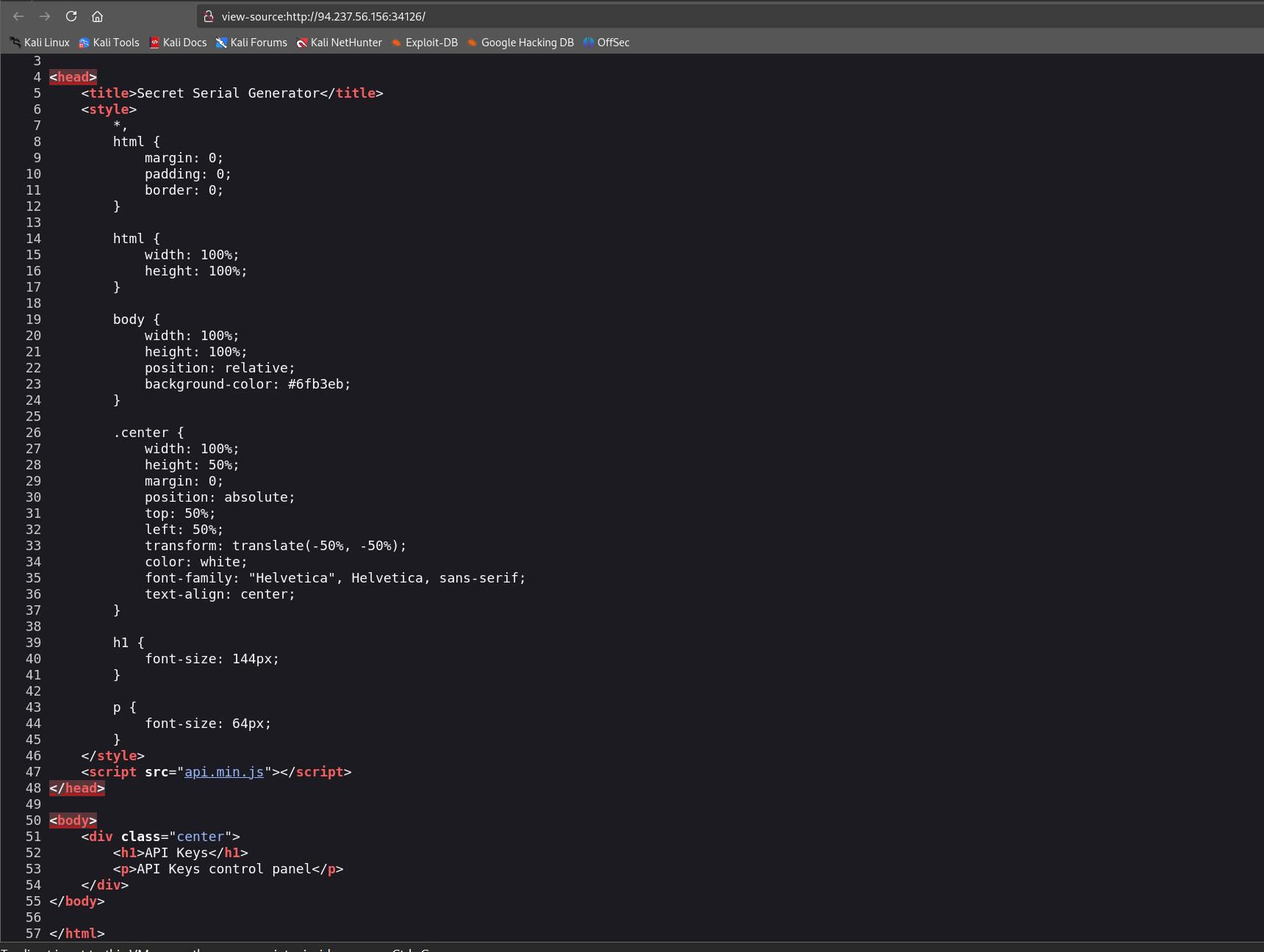
| |
This file contained obfuscated JavaScript.
Step 2: Running the JavaScript Code
After extracting the JavaScript file, I checked its contents. Running the script in a browser console produced unreadable output, indicating obfuscation.
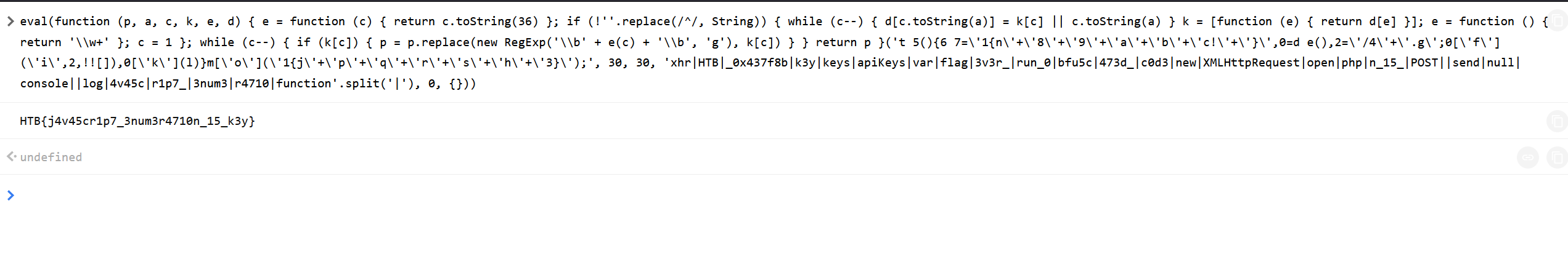
Step 3: Deobfuscating the JavaScript Code
I used an online JavaScript unpacker and manual formatting techniques to make the script readable. The deobfuscated script contained an API request:
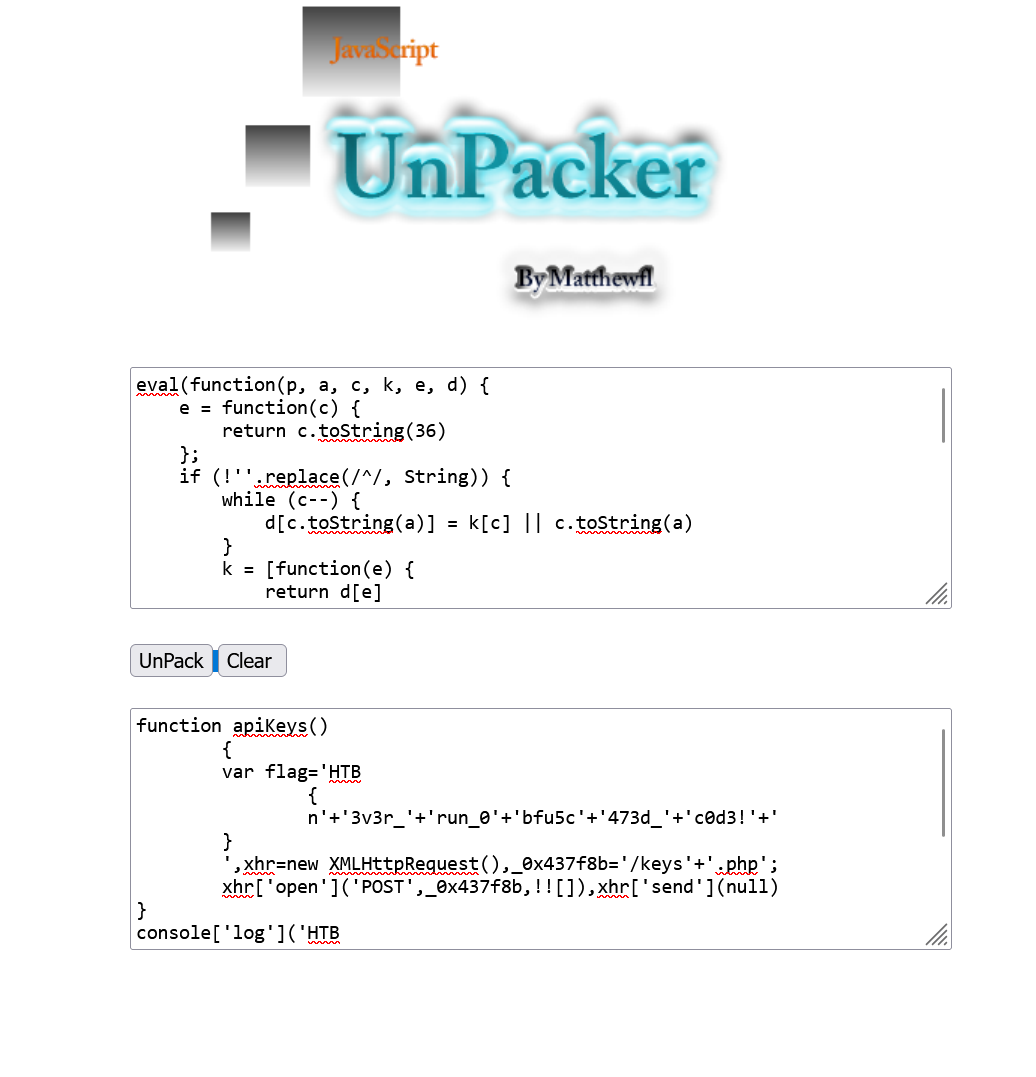
when I unpacked the code I could run it in the console so i had to fix it and run it.
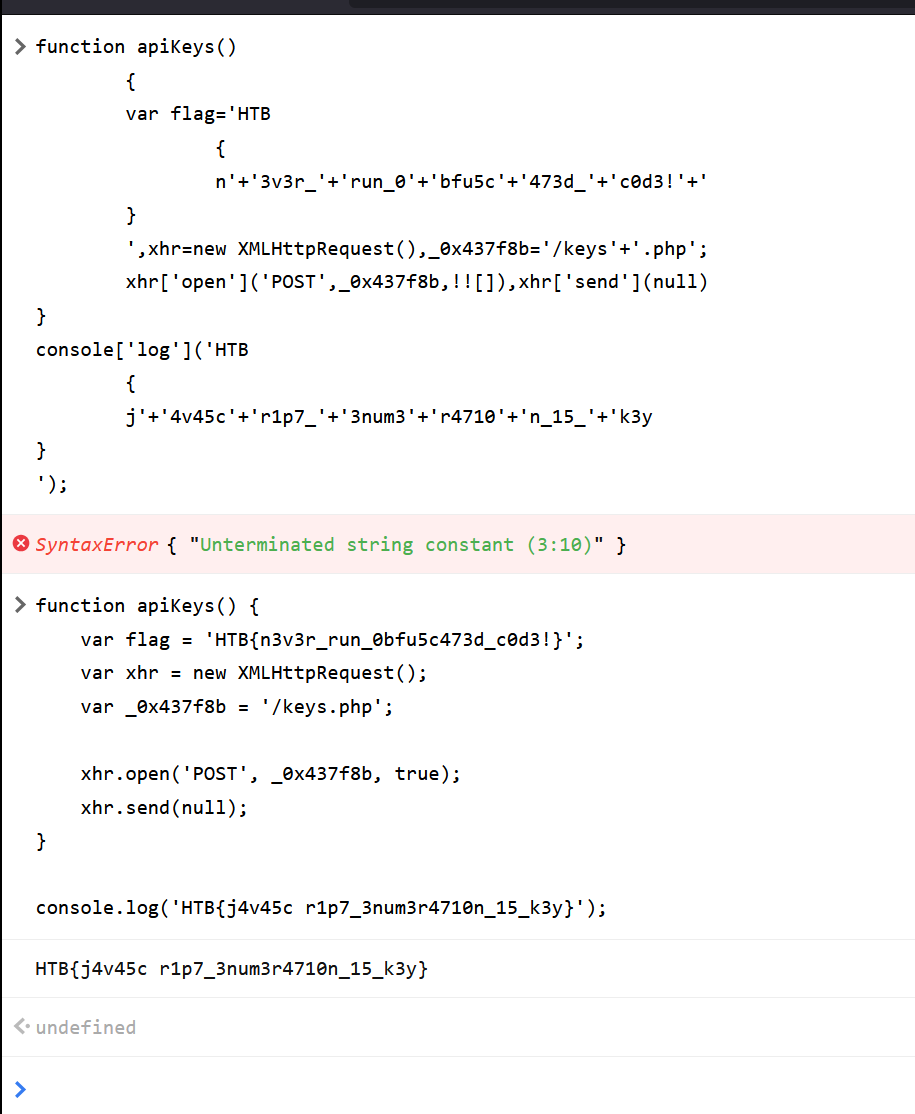
| |
From this, I know that keys.php was the endpoint handling API key validation.
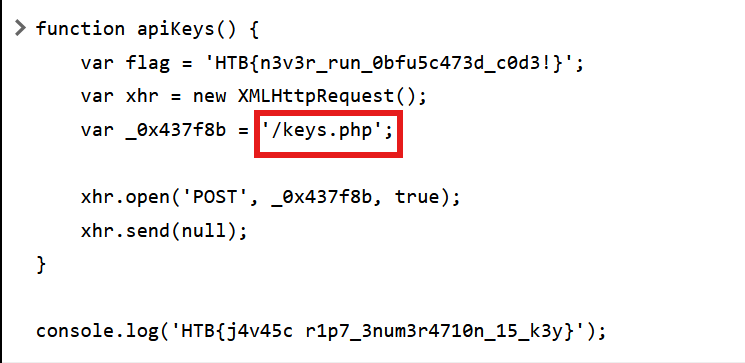
Step 4: Extracting and Decoding the Key
I sent a POST request to keys.php to retrieve the encoded key:
| |
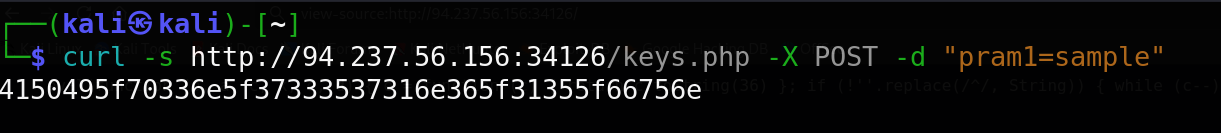 This returned an encoded string:
This returned an encoded string:
| |
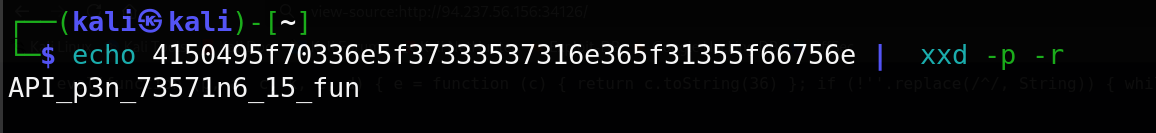
Using the command below, I decoded the hex string:
| |
The result:
| |
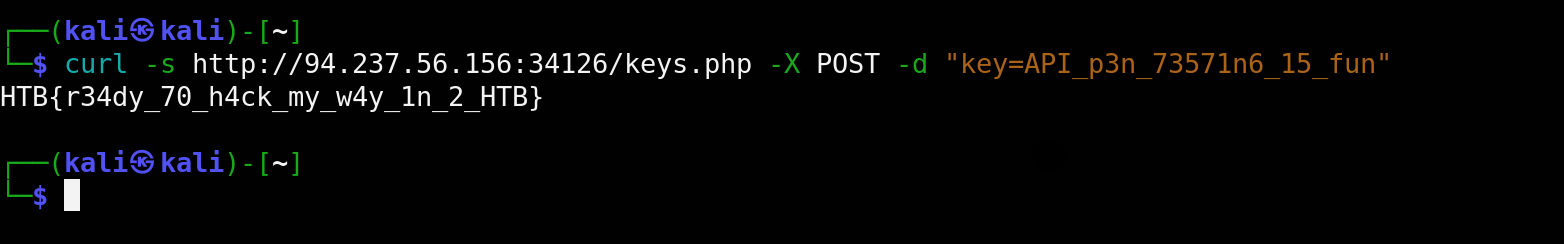
Step 5: Submitting the Key for the Final Flag
Now that I had the correct key, I sent another POST request:
| |
The response contained the final flag:
| |
This was a hands-on exercise in JavaScript Deobfuscation.